2019独角兽企业重金招聘Python工程师标准>>> 
关于iptables
什么是iptables?
常见于linx系统下的应用层防火墙工具
firewalld 和netfilter
Linux 防火墙-netfilter
- selinux 临时关闭 setenforce 0
- selinux 永久关闭 vi /etc/selinux/config
- centos7 之前使用 netfilter防火墙
- centos7 之后使用 firewalld防火墙
- 关闭firewalld 开启netfilter 方法
- systemctl stop firewalld
- systemctl disable firewalled
- yum install -y iptables-servicesx86_64
- systemctl enable iptables
- systemctl start iptables
示例
永久关闭selinux
[root@guo-001 ~]# vi /etc/selinux/config
# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
# disabled - No SELinux policy is loaded.
SELINUX=disabled·····这边关闭selinux 输入disabled
# SELINUXTYPE= can take one of three two values:
# targeted - Targeted processes are protected,
# minimum - Modification of targeted policy. Only selected processes are protected.
# mls - Multi Level Security protection.
SELINUXTYPE=targeted
查看selinux 是否关闭
[root@guo-001 ~]# getenforce
Disabled
临时关闭selinux
[root@guo-001 ~]# setenforce 0
setenforce: SELinux is disablednetfilter
centos 7 默认是关闭netfilter开启firewalld ,首先需要先关闭firewalld 并开启netfilter
关闭firewalld 开启netfilter
[root@guo-001 ~]# systemctl disable firewalld ······ 关闭firewalld开机启动
[root@guo-001 ~]# systemctl stop firewalld
······ 停止firewalld 这个服务
然后需要安装iptables 这个服务并开启
[root@guo-001 ~]# yum install -y iptables-services ······ 安装iptables 服务
[root@guo-001 ~]# systemctl enable iptables
····· 设置开机启动
Created symlink from /etc/systemd/system/basic.target.wants/iptables.service to /usr/lib/systemd/system/iptables.service.
[root@guo-001 ~]# systemctl start iptables
······ 开启iptables 服务iptables -nvL 查看防火墙的默认规则
[root@guo-001 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination 30 2068 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:220 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT 19 packets, 1620 bytes)pkts bytes target prot opt in out source destination netfilter 5表5链介绍
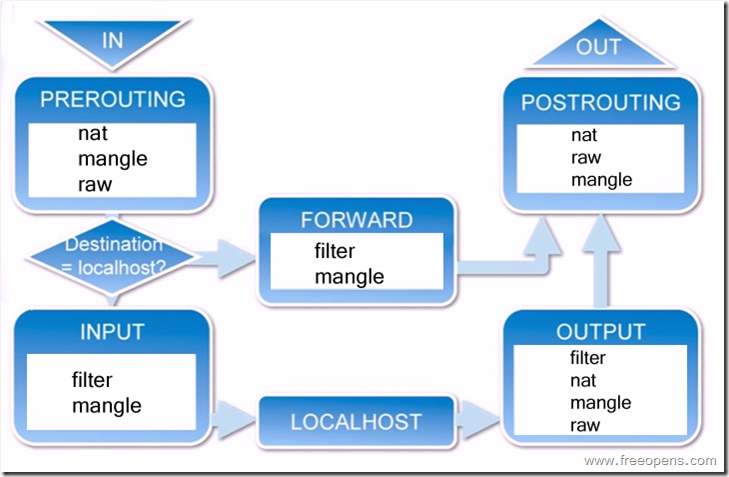
- netfilter5个表
- filter表:用于过滤包,最常用的表,有INPUT链(作用于进入本机的包)、OUTPUT链(作用于本机送出的包)、FORWARD链(作用于那些跟本机无关的包)三个链。
- nat表:网络地址转换,有PREROUTING链(包刚刚到达防火墙时改变它的目的地址)、OUTPUT链(改变本地产生的包的目的地址)、POSTROUTING链(包即将离开防火墙时改变其源地址)三个链。
- mangle表
- raw表
- security表
- netfilter5个链
- INPUT:通过路由表后目的地为本机
- OUTPUT:由本机产生,向外发出
- FORWARD:通过路由表后,目的地不为本机
- PREROUTING:数据包进入路由表之前
- POSTROUTING:发送到网卡接口之前
iptables传输数据包的过程
1、当一个数据包进入网卡时,它首先进入PREROUTING链,内核根据数据包目的IP判断是否需要转送出去。 2、 如果数据包就是进入本机的,它就会沿着图向下移动,到达INPUT链。数据包到了INPUT链后,任何进程都会收到它。本机上运行的程序可以发送数据包,这些数据包会经过OUTPUT链,然后到达POSTROUTING链输出。 3、如果数据包是要转发出去的,且内核允许转发,数据包就会如图所示向右移动,经过FORWARD链,然后到达POSTROUTING链输出。
iptables 语法
- 查看iptables规则:iptables -nvL
- iptables -F清空规则
- service iptables save 保存规则
- iptables -t nat //-t 指定表,默认是filter表
- iptables -Z 可以把计数器清零
- iptables -A INPUT -s192.168.5.1 -p tcp --sport 1234 -d 192.168.5.128 --dport 80 -j DROP
- iptables -I / -A / -D INPUT -s 1.1.1.1 -j DROP
- iptables -I INPUT -s 192.168.1.0/24 -i eth0 -j ACCEPT
- iptables -nvL --line-numbers
- iptables -D INPUT 1
- iptables -P INPUT DROP
iptables 规则保存文件 /etc/sysconfig/iptables
[root@xuexi-001 ~]# iptables -nvL······查看iptables规则
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination 430 33327 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 1 52 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:2268 6046 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT 372 packets, 47469 bytes)pkts bytes target prot opt in out source destination
[root@xuexi-001 ~]# iptables -F ······清空规则
[root@xuexi-001 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 6 packets, 396 bytes)
pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 4 packets, 400 bytes)
pkts bytes target prot opt in out source destination
iptables 默认保存的规则文件
[root@xuexi-001 ~]# cat /etc/sysconfig/iptables
# sample configuration for iptables service
# you can edit this manually or use system-config-firewall
# please do not ask us to add additional ports/services to this default configuration
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
查看nat 表规则
[root@xuexi-001 ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination
iptables -Z 可以把计数器清零
[root@xuexi-001 ~]# iptables -Z ;iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination 0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:220 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
# iptables -A INPUT -s 192.168.5.1 -p tcp --sport 1234 -d 192.168.5.128 --dport 80 -j DROP
- -A 添加一个规则
- -A INPUT针对INPUT 链添加一个规则
- -s 指定来源IP
- -p 指定协议(tcp,udp······)
- --sport 来源的端口
- -d 目标的IP
- --dport 目标的端口
- -j 操作方式
[root@xuexi-001 ~]# iptables -A INPUT -s192.168.5.1 -p tcp --sport 1234 -d 192.168.5.128 --dport 80 -j DROP
[root@xuexi-001 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination 117 9196 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:220 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited0 0 DROP tcp -- * * 192.168.5.1 192.168.5.128 tcp spt:1234 dpt:80Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT 16 packets, 1504 bytes)pkts bytes target prot opt in out source destination
# iptables -I INPUT -s 192.168.5.1 -p tcp --sport 80 -d 192.168.5.128 --dport 80 -j DROP
- -I 插入到规则的最前面,优先执行。
[root@xuexi-001 ~]# iptables -I INPUT -s 192.168.5.1 -p tcp --sport 80 -d 192.168.5.128 --dport 80 -j DROP
[root@xuexi-001 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destinat0 0 DROP tcp -- * * 192.168.5.1 192.168.501 36676 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 0 DROP tcp -- * * 192.168.5.1 192.168.Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destinat0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/Chain OUTPUT (policy ACCEPT 5 packets, 716 bytes)pkts bytes target prot opt in out source destinat
删除规则第一种方法
[root@xuexi-001 ~]# iptables -D INPUT -s 192.168.5.1 -p tcp --sport 80 -d 192.168.5.128 --dport 80 -j DROP
[root@xuexi-001 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination 653 48776 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:220 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited0 0 DROP tcp -- * * 192.168.5.1 192.168.5.128 tcp spt:80 dpt:80Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT 26 packets, 2408 bytes)pkts bytes target prot opt in out source destination
iptables -nvL --line-numbers 删除规则的第二种方法,先列出规则的编号,然后再使用 iptables -D INPUT 编号
[root@xuexi-001 ~]# iptables -nvL --line-numbers
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 741 54604 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
2 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
3 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
4 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
5 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
6 0 0 DROP tcp -- * * 192.168.5.1 192.168.5.128 tcp spt:80 dpt:80Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT 73 packets, 7792 bytes)
num pkts bytes target prot opt in out source destination
[root@xuexi-001 ~]# iptables -D INPUT 6
[root@xuexi-001 ~]# iptables -nvL --line-numbers
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 820 59864 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
2 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
3 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
4 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
5 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT 19 packets, 2812 bytes)
num pkts bytes target prot opt in out source destination
iptables filter 表小案例
[root@xuexi-001 ~]# vi /usr/local/sbin/iptables.sh
#!/bin/bash
ipt="/usr/sbin/iptables"
$ipt -F
$ipt -P INPUT DROP
$ipt -P OUTPUT ACCEPT
$ipt -P FORWARD ACCEPT
$ipt -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
$ipt -A INPUT -s 192.168.5.0/24 -p tcp --dport 22 -j ACCEPT
$ipt -A INPUT -p tcp --dport 80 -j ACCEPT
$ipt -A INPUT -p tcp --dport 21 -j ACCEPT
[root@xuexi-001 ~]# iptables -nvL
Chain INPUT (policy DROP 0 packets, 0 bytes)pkts bytes target prot opt in out source destination 110 7312 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED0 0 ACCEPT tcp -- * * 192.168.5.0/24 0.0.0.0/0 tcp dpt:220 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:800 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:21Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
[root@xuexi-001 ~]# service iptables restart
Redirecting to /bin/systemctl restart iptables.service
[root@xuexi-001 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination 34 2244 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:220 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT 18 packets, 1688 bytes)pkts bytes target prot opt in out source destination
[root@xuexi-001 ~]# ping www.qq.com
PING news.qq.com (182.254.50.164) 56(84) bytes of data.
64 bytes from 182.254.50.164 (182.254.50.164): icmp_seq=1 ttl=128 time=12.3 ms
64 bytes from 182.254.50.164 (182.254.50.164): icmp_seq=2 ttl=128 time=9.62 ms
^C
--- news.qq.com ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1003ms
rtt min/avg/max/mdev = 9.629/10.995/12.361/1.366 ms
[root@xuexi-001 ~]# iptables -I INPUT -p icmp --icmp-type 8 -j DROP
[root@xuexi-001 ~]# ping www.qq.com
PING news.qq.com (182.254.50.164) 56(84) bytes of data.
64 bytes from 182.254.50.164 (182.254.50.164): icmp_seq=1 ttl=128 time=10.9 ms
64 bytes from 182.254.50.164 (182.254.50.164): icmp_seq=2 ttl=128 time=10.1 ms
^C
--- news.qq.com ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 10.189/10.588/10.987/0.399 mswindows 上面ping linux ping不通
C:\Users\Administrator>ping 192.168.5.130正在 Ping 192.168.5.130 具有 32 字节的数据:
请求超时。
请求超时。
[root@xuexi-001 ~]# iptables -D INPUT -p icmp --icmp-type 8 -j DROP
iptables 规则组成
数据包访问控制
- ACCEPT:接收,允许通过
- DROP:丢弃,直接丢弃不查看
- REJECT:拒绝,不查看
数据包改写
- SNAT:源地址进行改写(发起端改写)
- DNAT:目标地址进行改写
信息记录
- LOG: 将对应的访问情况进行记录成日志
组成部分
iptables | table | command| chain|Parameter&Xmatch|target ---|---|--|--|--|--|-- iptables | -t filter/nat|-A |INPUT|-p tcp|-j ACCEPT iptables| | -D|FORWARD |-s | DROP iptables| | -L|OUTPUT |-d | REJECT iptables| | -F|PREROUTING |--sport | DNAT iptables| | -P|POSTROUTING |--dport | SNAT iptables| | -I| |--dports |
iptables| | -R| |-m tcp/state/multiport |
iptables| | -n| | |
- table : -t filter / nat 指定表
- command: -A :追加一条规则。 -D:删除。-L :显示当前规则。-F:将现有的规则进行清理。-P:设置默认的iptables 规则。 -I:插入一条规则,默认是第一条规则。
- chain:五条链
- Parameter&Xmatch:-p :指定协议。-s :发起源。 -d:目标地址 --sport:源端口。--dport:目标端口。--dports:端口段。
- target:ACCEPT:接收,允许通过。DROP:丢弃,直接丢弃不查看。REJECT:拒绝,不查看。
iptabels配置 场景一
规则一:对所有的地址开放本机的tcp(80、22、10-21)端口的访问
规则二:允许对所有的地址开放本机的基于ICMP协议的数据包访问
规则三:其他未被允许的端口禁止访问
iptables
-L :列出之前设置过的iptabels 规则 -n: 不显示主机名 -F:清除之前设置过的规则
[root@xuexi-001 ~]# iptables -F
[root@xuexi-001 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 28 packets, 1848 bytes)pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 15 packets, 1412 bytes)pkts bytes target prot opt in out source destination
规则一:对所有的地址开放本机的tcp(80、22、10-21)端口的访问
[root@xuexi-001 ~]# iptables -I INPUT -p tcp --dport 80 -j ACCEPT
[root@xuexi-001 ~]# iptables -I INPUT -p tcp --dport 22 -j ACCEPT
[root@xuexi-001 ~]# iptables -I INPUT -p tcp --dport 10:21 -j ACCEPT
[root@xuexi-001 ~]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- anywhere anywhere tcp dpts:10:ftp
ACCEPT tcp -- anywhere anywhere tcp dpt:ssh
ACCEPT tcp -- anywhere anywhere tcp dpt:httpChain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
规则二:允许对所有的地址开放本机的基于ICMP协议的数据包访问
[root@xuexi-001 ~]# iptables -I INPUT -p icmp -j ACCEPT
[root@xuexi-001 ~]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT icmp -- anywhere anywhere
ACCEPT tcp -- anywhere anywhere tcp dpts:10:ftp
ACCEPT tcp -- anywhere anywhere tcp dpt:ssh
ACCEPT tcp -- anywhere anywhere tcp dpt:httpChain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
规则三:其他未被允许的端口禁止访问
[root@xuexi-001 ~]# iptables -A INPUT -j REJECT
[root@xuexi-001 ~]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT icmp -- anywhere anywhere
ACCEPT tcp -- anywhere anywhere tcp dpts:10:ftp
ACCEPT tcp -- anywhere anywhere tcp dpt:ssh
ACCEPT tcp -- anywhere anywhere tcp dpt:http
REJECT all -- anywhere anywhere reject-with icmp-port-unreachableChain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
查看开启的服务端口
[root@xuexi-001 ~]# netstat -lnutp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 920/sshd
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 1116/master
tcp6 0 0 :::22 :::* LISTEN 920/sshd
tcp6 0 0 ::1:25 :::* LISTEN 1116/master
udp 0 0 127.0.0.1:323 0.0.0.0:* 543/chronyd
udp6 0 0 ::1:323 :::* 543
在第二台机器上进行扫描可以访问的端口
[root@localhost ~]# nmap -sS -p 0-1000 192.168.5.130Starting Nmap 6.40 ( http://nmap.org ) at 2018-06-16 16:44 CST
Nmap scan report for 192.168.5.130
Host is up (0.00048s latency).
Not shown: 987 filtered ports
PORT STATE SERVICE
10/tcp closed unknown
11/tcp closed systat
12/tcp closed unknown
13/tcp closed daytime
14/tcp closed unknown
15/tcp closed netstat
16/tcp closed unknown
17/tcp closed qotd
18/tcp closed unknown
19/tcp closed chargen
20/tcp closed ftp-data
21/tcp closed ftp
22/tcp open ssh
80/tcp closed http······因为在第一台机器上80端口之前并没有开启,所以这边是关闭状态。
MAC Address: 00:0C:29:B3:A2:BF (VMware)Nmap done: 1 IP address (1 host up) scanned in 17.72 seconds
这样设置后存在的问题:
1 本机无法访问本机
[root@xuexi-001 ~]# telnet 127.0.0.1 22
Trying 127.0.0.1...
^C
[root@xuexi-001 ~]# ping 127.0.0.1 22
PING 22 (0.0.0.22) 56(124) bytes of data.
^C
--- 22 ping statistics ---
4 packets transmitted, 0 received, 100% packet loss, time 2999ms
2本机无法访问其他主机
[root@xuexi-001 ~]# curl http://www.baidu.com
curl: (6) Could not resolve host: www.baidu.com; 未知的错误
解决方法:
1开放本机的回环地址
[root@xuexi-001 ~]# iptables -I INPUT -i lo -j ACCEPT
[root@xuexi-001 ~]# telnet 127.0.0.1 22
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
SSH-2.0-OpenSSH_7.4
Connection closed by foreign host.
2 iptables -I INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
[root@xuexi-001 ~]# iptables -I INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
[root@xuexi-001 ~]# curl -I http://www.baidu.com
HTTP/1.1 200 OK
Accept-Ranges: bytes
Cache-Control: private, no-cache, no-store, proxy-revalidate, no-transform
Connection: Keep-Alive
Content-Length: 277
Content-Type: text/html
Date: Sat, 16 Jun 2018 15:41:44 GMT
Etag: "575e1f60-115"
Last-Modified: Mon, 13 Jun 2016 02:50:08 GMT
Pragma: no-cache
Server: bfe/1.0.8.18
补充:只允许192.168.5.132 这台机器访问http服务
[root@xuexi-001 ~]# iptables -I INPUT -p tcp -s 192.168.5.132 --dport 80 -j ACCEPT
机器二192.168.5.132测试
[root@localhost ~]# telnet 192.168.5.130 80
Trying 192.168.5.130...
telnet: connect to address 192.168.5.130: Connection refused
iptables 规则备份和恢复
- service iptables save ······会把规则保存到/etc/sysconfig/iptables文件中
- 把iptables 规则备份到指定的文件中 my.ipt iptables-save > my.ipt
[root@xuexi-001 ~]# iptables-save > my.ipt
[root@xuexi-001 ~]# cat my.ipt
# Generated by iptables-save v1.4.21 on Sun Jun 17 00:10:39 2018
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [94:8140]
-A INPUT -s 192.168.5.132/32 -p tcp -m tcp --dport 80 -j ACCEPT
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -p tcp -m tcp --dport 10:21 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-port-unreachable
COMMIT
# Completed on Sun Jun 17 00:10:39 2018
- 恢复刚才备份的规则 iptables-restore < my.ipt
[root@xuexi-001 ~]# iptables -F
[root@xuexi-001 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination Chain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@xuexi-001 ~]# iptables-restore < my.ipt
[root@xuexi-001 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 192.168.5.132 0.0.0.0/0 tcp dpt:80
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpts:10:21
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachableChain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination