Overview of ISA and TMG Networking and ISA Networking Case Study (Part 1)
- Published: Dec 16, 2008
- Updated: Jan 21, 2009
- Author: Thomas Shinder
Pay close attention to the capitalization I use in this article. Network with a capital “N” refers to an ISA/TMG Firewall Network – which is a network objects that the firewall uses to define collections of IP addresses directly accessible from a specific network interface. In contrast, when a lower case “n” is used for network, I am referring to a generic network or network segment.

Figure 1

Figure 2

Figure 3

Figure 4

Figure 5

Figure 6
- The default External Network – the default External Network is defined by all IP addresses that are used by any other ISA Firewall Network. Any address that is not used by any other ISA Firewall Network will automatically be included as part of the default External Network. The NIC that defines the default External Network is usually the NIC with the default gateway bound to it. ISA and TMG MBE firewalls support a single default gateway
- The default Internal Network – this is the network you define during setup that represents your primary internal network. You can have multiple internal networks if you like, but there is .ly .e default Internal Network which you set up during installation of the ISA firewall. The default Internal Network typically contains your key infrastructure services, such as DNS, DHCP and Active Directory domain services. The default Internal Network is important because much of the ISA and TMG firewall’s System Policy is configured to access resources . the default Internal Network
- The Local Host Network – The Local Host Network is defined by the IP addresses bound to all NICs . the ISA or TMG firewall. For example, if the firewall had two interfaces, .e with IP address 2.2.2.2 bound to it and the other with 10.0.0.1 bound to it, then IP addresses 2.2.2.2 and 10.0.0.1 are members of the Local Host Network. Note that this breaks .e of the rules of ISA/TMG Networks – in that these IP addresses are also members of the Networks to which those NICs are connected. The 2.2.2.2 is likely a member of the default External Network and the 10.0.0.1 is a member of the default Internet Network.
- *** Clients Network – The *** Clients Network contains the IP addresses of connected *** clients. There are two ways to assign IP addresses to *** clients: using a static address pool and using DHCP. If you assign IP addresses to *** clients using a static address pool, then you must remove those IP addresses from any other Network that might contain them. For example, if you want to assign .-subnet addresses to *** clients (such as 192.168.1.200-192.168.1.225/24 when the internal interface is . 192.168.1.1/24), you must remove those addresses from the definition of the .-subnet network.
In contrast, if you want to use DHCP to assign IP addresses to *** clients, then you do not have to remove those addresses from the definition of any other Network that might also be using those addresses. It makes sense, since when you use DHCP to assign these addresses; you know that no other host should be able to use the same IP address . any other Network. In contrast, if you assign static addresses to *** clients, you do not know for sure that there might be an error that would lead you to use the same addresses . another Network. Addresses are automatically added and removed from the *** clients Network when they are used and released by the *** clients. Note that this represents a second exception to our rule that an IP address can belong to a single Network – since you use DHCP to assign IP addresses to *** clients, those addresses can belong to another ISA/TMG Firewall Network. - Quarantined *** Clients Network – The Quarantined *** Clients Network contains the IP addresses of *** clients that have not yet passed *** quarantine control. This is configured as a separate Network from the *** Clients Network because you might want to create Firewall Rules that allow quarantined *** clients access to resources . a Protected Network (a Protected Network is any ISA/TMG Network that isn’t the default External Network) or even . the Internet so that they can remediate themselves. IP addresses are automatically moved from the Quarantined *** Clients Network to the *** Clients Network when the *** client passes quarantine control checks.

Figure 7
- ISA/TMG Firewall Networks are used for spoof detection. If a source IP address arrives at an interface that is a root of an ISA Firewall Network that isn’t an IP address defined for that Network, then the connection attempt is dropped as a spoofed connection attempt
- An IP address can be assigned to a single ISA/TMG Firewall Network. The .ly exceptions to this rule are seen with the Local Host Network and the *** Clients and Quarantined *** Clients Networks when you use DHCP to assign addresses to *** clients.
- An ISA/TMG Firewall Network can contain IP addresses from multiple network IDs. What all these IP addresses have in common is that if they need to connect to and through the ISA or TMG firewall through the same NIC
- Enables communications between the two ISA/TMG Firewall Networks
- Sets a routing relationship between the two Networks
相关文章:
阿里云免费开放一切AI算力,加速新型冠状病毒新药和疫苗研发
近日,阿里云宣布,为了帮助加速新药和疫苗研发,将向全球公共科研机构免费开放一切AI算力。目前,中国疾控中心已成功分离病毒,疫苗研发和药物筛选仍在争分夺秒地进行。新药和疫苗研发期间,需要进行大量的数据…

ASP.net(C#)批量上传图片(完整版)
来自:http://blog.itpub.net/9869521/viewspace-667955/ 这篇关于ASP.Net批量上传图片的文章写得非常好,偶尔在网上看到想转载到这里,却费劲了周折。为了更新这篇文章,我用了近半个小时,网上的转载都残缺不全ÿ…

码农技术炒股之路——任务管理器
系统任务和普通任务都是通过任务管理器调度的。它们的区别是:系统任务在程序运行后即不会被修改,而普通任务则会被修改。(转载请指明出于breaksoftware的csdn博客) 为什么要有这样的设计?因为我希望它是一个可以不用停…
面对新型肺炎疫情,AI能做什么?
作者 | 马超出品 | AI科技大本营(ID:rgznai100)根据最新的新型冠状病毒疫情通报,截至1月30日24时,国家卫生健康委公布确诊病例9692例,重症病例1527例,累计死亡病例213例,另有疑似病例15238例。为…

大家帮忙.谢谢!..(急急急急急)
大家帮忙.谢谢!..(急急急急急) Delphi / Windows SDK/APIhttp://www.delphi2007.net/DelphiDB/html/delphi_20061218224617231.htmlprocedure TForm1.Button4Click(Sender: TObject); var P : pstring; i, j : integer; begin GetMem(p, sizeof(stri…

HDU4866 Shooting (要持久段树)
意甲冠军: 给你一些并行x行轴。总是询问坐标x的顶部之前,k一个段高度,。标题是必须在线。思路: 首先要会可持久化线段树(又称主席树和函数式线段树)。不会的能够去做下POJ 2104。 把全部线段高度离散化,作为结点建线段…
C++过去的这一年
作者 | Bartek译者 | 苏本如,责编 | 屠敏出品 | CSDN(ID:CSDNnews)【导读】本文旨在让我们回顾 C 2019年里的变化和发展!我们将重点关注本年度里 C 上发生的重大事件,标准的发展,工具的变化等等…

码农技术炒股之路——抓取股票基本信息、实时交易信息、主力动向信息
从本节开始,我们开始介绍各个抓取和备份业务。(转载请指明出于breaksoftware的csdn博客) 因为我们数据库很多,数据库中表也很多,所以我们需要一个自动检测并创建数据库和表的功能。在《码农技术炒股之路——数据库管理…

TemplateBuilder
http://msdn.microsoft.com/zh-cn/vstudio/system.web.ui.templatebuilder_members(VS.85).aspx TemplateBuilder 成员TemplateBuilder 成员支持在生成模板及其包含的子控件时使用的页分析器。 下表列出了由 TemplateBuilder 类型公开的成员。 公共构造函数 名称 说明 Templat…

【iOS UI】iOS 9 GUI 资源分享
分享的内容包括一个【DesignCode-iOS-9-GUI】Sketch 文件, 和苹果官方释出的【SF-UI、SF-Compact】两种字体的安装包。 以上内容是正版、免费的 <a href "https://itunes.apple.com/cn/app/sketch-3/id852320343?mt12">Sketch</a> 是收费软…
反向R?削弱显著特征为细粒度分类带来提升 | AAAI 2020
作者 | VincentLee来源 | 晓飞的算法工程笔记导读:论文提出了类似于dropout作用的diversification block,通过抑制特征图的高响应区域来反向提高模型的特征提取能力,在损失函数方面,提出专注于top-k类别的gradient-boosting loss来…

C#初学——doWhile
继续上面的学习,这次的是流程控制,用dowhile,代码如下,还是用语言选择来作为事例的。using System; using System.Collections.Generic; using System.Text; namespace ConsoleApplication9 { class Program { static void Main(s…

码农技术炒股之路——实时交易信息、主力动向信息分库备份
一般来说,一个股票信息应该保存在一张表中。但是由于我机器资源限制,且我希望尽快频率的抓取数据。所以每天我将所有股票的实时交易信息放在daily_temp库中的一个以日期命名的表中。主力动向信息也是如此。但是盘后分析股票时,我们会以单只股…

数据预处理(完整步骤)
原文:http://dataunion.org/5009.html 一:为什么要预处理数据?(1)现实世界的数据是肮脏的(不完整,含噪声,不一致)(2)没有高质量的数据,…

码农技术炒股之路——抓取日线数据、计算均线和除权数据
日线数据是股票每日收盘后的信息。这块数据不用实时抓取,所以并不占用宝贵的交易时间的资源。于是我们抓取完数据后直接往切片后的数据库中保存。(转载请指明出于breaksoftware的csdn博客) 抓取日线数据 我们先要获取今天有交易信息的股票代…

茫茫碌碌的日子
一连很好多天,都在为公司数据库基础构架升级的事情忙活着。升级的事情还是比较棘手的。需要升级硬件服务器,相关的存储,操作系统,数据库产品,涉及面非常多。当然烦心的事情就很多。作为线上生产系统,升级和…
Python PK C++,究竟谁更胜一筹?
作者 | Farhad Malik译者 | 弯月,编辑 | 屠敏来源 | CSDN(ID:CSDNnews)在编程生涯的早期阶段,我参与过一款C数学优化应用程序的开发,这个程序对性能的要求很高。至今我依然记得那段艰难的经历。在那个项目中…

oracle--查看表空间大小以及修改表空间大小
为什么80%的码农都做不了架构师?>>> 一.修改表空间大小 解决以上问题的办法:通过增大表空间即可解决,如下: Sql代码 使用dba用户登陆 sqlplus / as sysdba; 执行如下命令: SQL >…
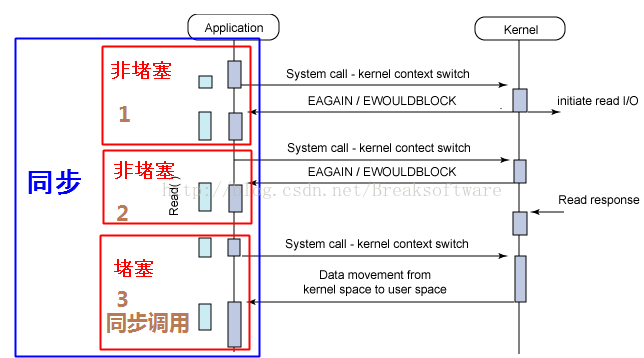
同步、异步、堵塞、非堵塞和函数调用及I/O之间的组合概念
在我们工作和学习中,经常会接触到“同步”、“异步”、“堵塞”和“非堵塞”这些概念,但是并不是每个人都能将它们的关系和区别说清楚。本文将对这些基本概念进行讨论,以期让大家有更清楚的认识。(转载请指明出于breaksoftware的c…
“抗击”新型肺炎!阿里达摩院研发AI算法,半小时完成疑似病例基因分析
利用技术辅助抗击疫情,阿里巴巴、百度等科技巨头各显身手。此前,AI科技大本营采访报道了阿里达摩院《数十名工程师作战5天,阿里达摩院连夜研发智能疫情机器人》一文,后者为了解决客服人力不足的局面,快速响应政府需求开…

反编译工具jad简单用法
反编译工具jad简单用法 下载地址:[url]http://58.251.57.206/down1?cidB99584EFA6154A13E5C0B273C3876BD4CC8CE672&t2&fmt&usrinput[/url]反编译工具jad &dt2002000一. 不用安装,只要解压就行(有这样两个文件jad.exe&#x…
ubuntu 系统设置bugzilla制
随着时间的推移。在大脑中形成的记忆总会慢慢的淡去。人的记忆力就是这样。所以最好的办法就是形成博客去记录下来,一方面给自己以后回想用。一方面也算是自己的一个积累。所以一旦选择了一个行业,最好不要轻 易转行,由于非常多知识须要不断的…
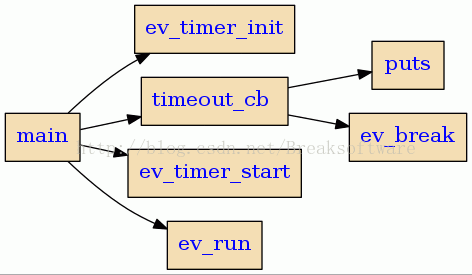
静态分析C语言生成函数调用关系的利器——cflow
除了《静态分析C语言生成函数调用关系的利器——calltree》一文中介绍的calltree,我们还可以借助cflow辅助我们阅读理解代码。(转载请指明出于breaksoftware的csdn博客) cflow的说明和安装cflow是一款静态分析C语言代码的工具,通过…
我在MongoDB年终大会上获二等奖文章:由数据迁移至MongoDB导致的数据不一致问题及解决方案...
作者 | 上海小胖来源 | Python专栏(ID:xpchuiit)故事背景企业现状2019年年初,我接到了一个神秘电话,电话那头竟然准确的说出了我的昵称:上海小胖。我想这事情不简单,就回了句:您好,我是小胖&…

注意String.Split的几个重载形式
String.Split应该是经常用到的一个函数了,经常的有下面两种形式 public string[] Split(char[] separator, StringSplitOptions options); public string[] Split(string[] separator, StringSplitOptions options); 1. 多数情况下我们会使用第一种,代码里可能这…

如何让猎头找到你
如何让猎头找到你

libev源码解析——总览
libev是个非常优秀的基于事件的循环库,很多开源软件,比如nodejs就是使用其实现基础功能。本系列将对该库进行源码分析。(转载请指明出于breaksoftware的csdn博客) 不知道是被墙了还是网站不再维护,它的官网(…
GPT-2仅是“反刍”知识,真正理解语言还要改弦更张
作者 | Gary Marcus译者 | 泓技编辑 | 夕颜出品 | AI科技大本营(ID:rgznai100)【导读】OpenAI的GPT-2正被广泛地讨论,无论是《纽约客》还是《经济学人》,我们都能看到有关它的话题。关于自然和人工智能,它想…

sap business one 笑谈
Sap Business .e 出生在以色列,生下来的时候父母给起了个小名叫SBO,据说他的亲生父母是SAP家庭里的一个重要成员,后来SAP家族里的长老认为SBO长得不错,挺好看的。毕竟SAP家族里生下来的儿子都是胖胖的,想要个瘦点长相好…

来51学院的第一天
【来51学院的第一天】转载于:https://blog.51cto.com/10801189/1703279
