提取Jar2Exe源代码,JavaAgent监控法
链客,专为开发者而生,有问必答!
此文章来自区块链技术社区,未经允许拒绝转载。

最近遇见一个麻烦,明明知道是java写的小软件,但是打包成了exe,木得办法,之前打包的都有缓存能在TEMP文件夹找到。这次可不一样了,特此记录一下。
为此特地搜集了一些java打包成exe的软件。
一、exe4j。
说明:exe4j可以将Jar文件制作成exe文件,但需jre支持,也可将Jar文件放在外面。
软件性质:共享软件
下载地址:http://www.ej-technologies.com/products/exe4j/overview.html
二、JBuilder。
说明:新版本的JBuilder可以直接把工程制作成各系统的可执行文件,包括Windows系统。
软件性质:商业软件
下载地址:略。我是从eMule下载的。
三、NativeJ。
说明:与exe4j功能类似。
软件性质:共享软件
下载地址:http://www.dobysoft.com/products/nativej/download.html
四、Excelsior JET。
说明:可以直接将Java类文件制作成exe文件,除AWT和Swing及第三方图形接口外可不需jre支持(Java5.0不行)。
软件性质:共享软件
下载地址:http://excelsior-usa.com/home.html
五、jshrink。
说明:可将Jar文件打包进exe文件。同时具有混淆功能(这才是它的主要功能)。
软件性质:共享软件
下载地址:http://www.e-t.com/jshrink.html
六、InstallAnywhere。
说明:打包工具,对Java打包最好用。可打包成各操作系统运行包。包括Windows系统。
软件性质:商业软件。
下载地址:http://www.zerog.com/
七、InstallShieldX。
说明:与InstallAnywhere类似,但比InstallAnywhere功能强大。相对的,比较复杂,不易上手,我现在还没学会。
软件性质:商业软件。
下载地址:http://www.installshield.com/
八、Jar2Exe.
这是今天特地要说的java打包成EXE的软件
下载地址:http://www.jar2exe.com/
Jar2Exe
明文:简单的打包方式,解压软件解压一下所有Class文件都在里面。
隐藏,Jar包会被经过简单的加密之后存储在EXE程序中的资源内。
加密+隐藏:Jar包会被加密,并且所有文件名都会被哈希,之后存储在EXE程序资源中,这是最常见的一种加密,也是最麻烦的一种提取方式。
面对后两种情况下,通常来说,我们如果想要提取完整的jar包,必须用ODB调程序执行到解密完成调用jar的位置,然后dump内存把所有内容dump下来。
这里学习一种方法(但是方法有一定缺点,我们后面讲把)
首先构建一个Java代理(JavaAgent),目的是让程序员可以更加灵活的监控Java虚拟机的运行。我们要实现的是监控ClassLoader,在它要加载一个类的时候,dump出这个类来并写入一个jar文件中。
然后激活该JavaAgent,接着运行Jar2Exe编译的Exe程序。尽可能多的测试程序中的功能,点击不同的按钮,让更多的类文件被加载到内存中,这样它们就会被dump出来。
但是缺点是很明显的
1.如果class没有加载就dump不到了
2.jar中的图片、音频等资源是得不到的。
重点来了!下面讲步骤
1.准备工作
下载地址:https://github.com/HaoQinLandv/e2j
然后放到同一个目录下
打开命令行并进入要破解的程序所在目录,在命令行输入以下命令设置JavaAgent的加载
set JAVA_TOOL_OPTIONS=-javaagent:e2j-agent.jar
该命令是让java程序在加载一个类时会自动调用JavaAgent
2.操作
命令行运行你需要提取源代码的软件即可。
这种方法有缺陷,但是最简单的办法,下面来看国外大神如何提取的。
http://reverseengineeringtips.blogspot.com/2014/12/unpacking-jar2exe-21-extracting-jar.html
这个连接天朝境内无法访问。
=========================================================================================
这里是分割线
==========================================================================================
Unpacking Jar2Exe 2.1: Extracting The Jar File At All 3 Protection Levels
Welcome to this extensive tutorial for unpacking Jar2Exe. Jar2Exe is a java executable wrapper which works by taking your original java archive, wrapping it into an executable, and executing it through a virtual environment using the jvm.dll provided with each java distribution. It also provides the ability to hide your archive and encrypt the class names making recovery difficult. The goal of this tutorial is to demonstrate how to recover a jar file at the 3 different protection levels provided by Jar2Exe.
In this tutorial, I will be using the file SimpleApp.jar which is included with launch4j. You can protect it with the same settings to reverse along with me.
Tools Needed:
Resource Hacker
Winhex
Ollydbg 1.10+ MemoryDump 0.9 and Olly Advanced or StrongOD Plugin(for advanced ctrl+g).
DJ Java Decompiler
7-Zip or Winrar
Jar2Exe Level 1: No Hiding, No Encryption:
This is the default wrapping level which provides no protection to your java file. As you can see, the Hide class files and Encrypt and hide class files options are left unchecked. This level of protection simply takes your java archive/jar file, concatenates it to the end of the executable, and embeds its java files inside of it. This java archive can be recovered using a hex editor, just like we did with launch4j in the previous tutorial. To begin, we will open sample file called ‘SimpleAppNoHide.exe’ in winhex. To find the archive, scroll to the bottom of the file. Another option you can try other than scrolling is to search for the ascii string "serial "(with the space). This should take you directly to the archive, but I cannot guarantee that this approach will always be successful.
Once you are here, the first occurrence of ‘PK’ labels the start of our archive. We can label this as our beginning of block:
Once you have done so, right click the selected block and click Edit. In the new pane, go to Copy Block -> Into New File.
Afterwards, we can save it as a jar file. I used the name SimpleAppNoHide.jar:
Once we are finished, the program will run correctly, but to be tidy, we need to delete the extra files that Jar2Exe added to our archive. Let’s open the archive in 7-zip or winrar(whichever you fancy).
Once it is opened, you can see that Jar2Exe adds an additional directory called ‘com’. While some other java applications may use this directory, Jar2Exe adds an additional subdirectory called regexlab.
After entering the com directory, we see that regexlab is the only subdirectory it contains, meaning that the entire com folder is unused and can simply be deleted from the archive, let’s go ahead and delete it:
After confirming the deletion, we can close the archive and run the jar file.
If you did everything correctly, the application should run without problems and our work is finished.
Jar2Exe Level 2: Hidden Archive:
With the level 2 protection, Jar2Exe takes our java archive, encrypts it, and adds it as an RCData entry in the resource directory. To find the offset of the encrypted archive, we need to open our executable which I named ‘SimpleAppHide.exe’ in a resource editor. For this, I prefer resource hacker:
Above, we have located the encrypted data in the “RCData” section of the resource table. In this case, our offset is 46398h. Keep a note of this and open the application in Ollydbg. Once you have it opened, go to the hex dump section and go to the offset above:
Once you arrive at the offset, right click the byte and add a Hardware Breakpoint On Access -> Byte:
Now, let’s run the program and wait for the break to occur. We should arrive here:
This loop will decrypt our archive byte for byte. Let’s toggle a breakpoint on the instruction after the loop. In this example, the instruction is 00401BE3 > CMP DWOR PTR SS:[ESP+18],EBP. Run the program now and let the decryption complete. Once we break here, the register EAX will contain the location where our decrypted jar file is located and ECX contains its size. Using this information, we are ready to dump the file from memory. To do this, I found a very simple plugin called Memory Dump. It allows you to simply specify a memory address and size to dump those bytes to disk. Let’s open the plugin:
To begin, check the field which says End Address / Lenght. This will allow us to enter the length value. Set the Start Address to the value in EAX and the lenght(length) equal to the value in ECX. In my case, the address is 296810 and the size is 11EC. Once you have entered these values, we are ready to dump this to disk.
A limitation of this tool is that you can only save the file with a .dmp extension, but we can easily rename it once we are finished. Simply save it with the name you fancy. In this case I named it as SimpleApp3Hide.dmp for easy recognition.
After a quick renaming, the file is ready to run.
Jar2Exe Level 3: Hidden Archive + Encrypted Class Names:
This is the strongest protection offered by Jar2Exe. First, it changes all of the class file names to gibberish. Second, it encrypts and hides the files just like the level 2 protection. While we can recover the archive with a similar method as in Level 2, we need to take an additional step to repair the class names.
To begin, let’s open the application “SimpleAppEncrypt.exe” in a resource editor just as before to acquire the offset of the encrypted RCData:
Our offset in this case is 49398h. Let’s note that and open the application in Ollydbg and follow the offset
Once we arrive at the offset, place a hardware breakpoint on access-> byte just like before.
Run the program an wait for the breakpoint. We should arrive at the following code:
This is the new decryption routine. The instruction 0040ACED-> MOV BYTE PTR DS:[ECX],AL will move each decrypted byte to their new memory location.
According to the code, the address of the memory location where our file is decrypted to can be found at the stack pointer [ESP+18]
The value at ESP+1C contains the size of the memory region. This can be verified by checking the decrement value of the loop.
This code verifies that ESP+1C is the value decremented. ESP+1c is moved to EAX, decremented, and then moved back.
At our current location where the hardware breakpoint landed us, the values at ESP +18 and ESP+1C are the ones we need for our dump. Please note them and target a breakpoint on the instruction outside of the loop.
Once you break here, we are ready to make a dump of the file. But first, I would like to show you the encrypted strings in our archive to give you a glimpse of how jar2exe encrypts them:
As you can see here, the names of our classes and manifest files have been completely obfuscated. As a result, we need to recover these names manually. The way that jar2exe gets the original names for the class is to read them directly from the class file itself. I will show you a simple approach to doing this once we dump the archive.
Now since I am finished digressing, let’s dump the file just like before.
In my case, the location of the decrypted file is at 296858 and its length is 1284. We are ready to dump.
Now that we have saved the file, let’s rename change the extension to .jar and prepare to extract the contents.
Please note that due to the encryption employed on the names, the file will not run until we correct the classes. Let’s extract the contents to a new folder so we can begin repairing.
Once we have extracted the files, let’s open the new directory and see the files.
As we can see here, the file names are complete gibberish. The randomly named directories will typically not contain a file and can be deleted. The rest of the files will be the original class and manifest files. To begin the recovery, I like to first identify which file is the manifest. We can usually assume that the manifest will be the smallest file contained in the archive. The manifest.mf file tells the java runtime which file contains the main() class. Without it, the runtime would not know how to execute the code. Let’s find the smallest file and open it in a text editor.
As you can see, we have identified our manifest file. This file should be renamed to ‘MANIFEST.MF’ and placed in a subdirectory called ‘META-INF’. Remember that these names are case sensitive and must be typed in all uppercase.
To continue with the rest of the files, let’s add a ‘.class’ extension to each of them and open them in your favorite java decompiler. You can read these names with a hex editor if you fancy, but a decompiler makes it a little cleaner. Let’s begin with the largest file which is 4kb. I will open it in DJ Java Decompiler
As we can see here, we have identified the name of this class file as SimpleApp which according to the manifest, contains our main() procedure. The name of the package this file resides in is ‘net.sf.launch4j.example’. The dots between these words represent a subdirectory. That means that this class belongs in a folder hierarchy of net/sf/launch4j/example. Let’s rename this to class file to ‘SimpleApp.class’, create the directory hierarchy listed above, and place this file in it.
Now that we have completed this, we just need to go back and follow the same steps for the rest of the files. Please remember that every name is case sensitive. Once you have recovered each of them and placed them into the correct directory(there is only one directory), it should look like this:
Now that we are done, it is time to recreate the jar file. A jar file is simply a zip archive under a different extension. All we need to do is go back to the directory that contains our two folders named ‘net’ and ‘META-INF’ and add them to a zip archive.
Now, we simply change the extension of the zip archive to jar and it is ready to run.
Now let’s see the finished result
I hope that you have learned a few things from this tutorial and have walked away with some new knowledge. If something in this tutorial is not clear, please feel free to post a comment and I will try to explain it further. Until next time, happy reversing.
============================================================================================
我也用OD试了一下,可能是因为不会用的问题吧,拖入进去木有反应,SO放弃了老外这种方法了。
相关文章:

并发编程之多进程
一 multiprocessing模块介绍 python中的多线程无法利用多核优势,如果想要充分地使用多核CPU的资源(os.cpu_count()查看),在python中大部分情况需要使用多进程。Python提供了multiprocessing。 multiprocessing模块用来开启子进…

x9此计算机上没有hasp_mastercam x9安装步骤
大家好,我是时间财富网智能客服时间君,上述问题将由我为大家进行解答。mastercam x9安装步骤是:1、首先,先下载好mastercam软件,下载安装包的大小为3.01G,双击打开setup.exe安装文件,然后再安装…

bitcoinj开发环境搭建
链客,专为开发者而生,有问必答! 此文章来自区块链技术社区,未经允许拒绝转载。 bitcoinj开发包是一个Java版本的比特币协议实现,使用bitcoinj就可以实现钱包管理和交易的发送与接收,而无须本地安装bitcoin…

static关键字用法
static关键字 1.修饰成员变量 在我们平时的使用当中,static最常用的功能就是修饰类的属性和方法,让他们成为类的成员属性和方法,我们通常将用static修饰的成员称为类成员或者静态成员,这句话挺起来都点奇怪,其实这是相…

swift x输入流_SwiftUI 探索 - 状态和数据流
SwiftUI是iOS13新出的声明式UI框架,将会完全改变以前命令式操作UI的开发方式。此文章主要介绍SwiftUI中状态管理的方式。可变状态State与React和Flutter中的State类似,只不过React和Flutter中需要显式调用setState方法。在SwiftUI 中直接修改State属性值…

qt 控件 背景色 透明 除去边框
在调试ui的时候,需要将背景色变为透明,与母控件的颜色一致,并且除去边框。 参考链接: http://www.qtcentre.org/threads/12148-how-QTextEdit-transparent-to-his-parent-window 除去背景色,使透明。ui->textBrowse…

A Strange Bitcoin Transaction
链客,专为开发者而生,有问必答! 此文章来自区块链技术社区,未经允许拒绝转载。 在之前的谈谈比特币的地址安全问题这篇文章中,我们谈到一个名为”LBC”的项目,这个项目通过暴力碰撞企图打捞到一些什么东西…

Jsoncpp 使用方法解析
Jsoncpp是目前比较好用的开源Json解析库,现在总结一下它的使用方法,理解,以供以后查阅。 在引入Jsoncpp的时候我们看到Jsoncpp里边的常用的cpp文件,有json_reader.cpp,json_value.cpp,json_writer.cpp, 其中: json_val…

tomcat限速_WEB服务的下载限速(二)(限速模块安装与配置)
一、准备工作1、下载mod_bw-0.92.tgz2、安装httpd-develyum install httpd-devel二、安装限速模块tar -xvf mod_bw-0.92.tgzapxs -c -i -a mod_bw.c三、配置apachevim /usr/local/apache/conf/httpd.conf查看是否已加载 LoadModule bw_module modules/mod_bw.so如果没…
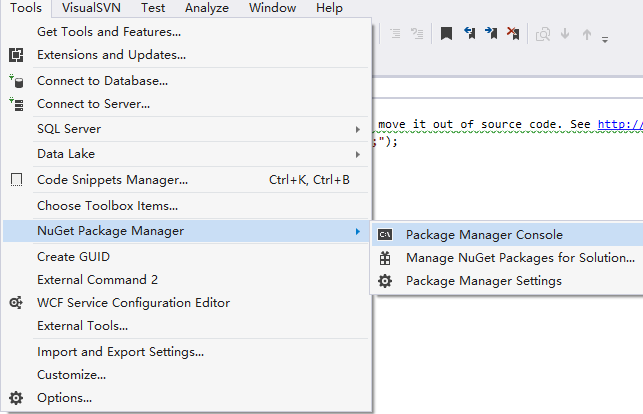
EntityFrameworkCore 安装
映射现有(多个)数据库: 安装Microsoft.EntityFrameworkCore最新版本Tools -> NuGet Package Manager -> Package Manager Console 分别输入: Scaffold-DbContext "Server.;DatabaseSxh;Trusted_ConnectionTrue;" …

python神秘的魔法函数_Python魔法函数
1.什么是魔法函数魔法函数即Python类中以__(双下划线)开头,以__(双下划线)结尾的函数,Python提供的函数,可让咱们随意定义类的特性示例:class Company(object):def __init__(self, employee_list):self.employee employee_listde…

HDU-4738-Caocao's Bridges(tarjan)
转载于:https://www.cnblogs.com/GrowingJlx/p/6642692.html

博客园美化技巧汇总
首先得有js权限 1.1 页脚js代码 <script type"text/javascript"> /*功能:生成博客目录的JS工具测试:IE8,火狐,google测试通过zhang_derek2018-01-03 */ var BlogDirectory {/*获取元素位置,距浏览器左…

数据事务四种隔离机制和七种传播行为
数据事务四种隔离机制和七种传播行为 一、隔离级别: 数据库事务的隔离级别有4个,由低到高依次为Read uncommitted、Read committed、Repeatable read、Serializable,这四个级别可以逐个解决脏读、不可重复读、幻读这几类问题。 1.…

vue注册新节点_vue怎么重新组装slots节点
在后台列表中通常会有比较多的操作按钮 过多的按钮影响布局 也影响操作 因此想通过vue的组件来控制显示的按钮个数 多余的按钮自动被收进一个特殊的 更多 按钮里面,效果图:组件定义:Vue.component(button-groups, {render(createElement) {re…

什么是EOS?
链客,专为开发者而生,有问必答! 此文章来自区块链技术社区,未经允许拒绝转载。 关于EOS有很多炒作。2017年5月,EOS的创始人丹•拉莫(Dan Larimer)在纽约宣布这一消息时,一幅巨大的巨型屏幕广告在时代广场上…

【GDKOI2016Day1T1-魔卡少女】【拆位】线段树维护区间内所有连续子区间的异或和...
题意:给出N个数,M个操作。操作有修改和询问两种,每次修改将一个数改成另一个数,每次询问一个区间的所有连续子区间的异或和。n,m<100000,ai<1000 题解: 当年(其实也就是今年)做不出来的题…

用composer安装laravel-bjyblog
前面讲了两行命令composer的安装,现在我们来操作一下composer安装基于laravel的博客laravel-bjyblog。测试环境是linux,bt面板,php7.2安装扩展fileinfo/opcache/redis/imagemagick/imap/exif,禁用 proc_open 函数 下面开始安装&am…

微信小程序多项选择器_微信小程序三级联动之多列选择器
有些时候,三级联动业务场景并不只是全国地区选择,可能还涉及到自定义分类的三级联动,这时就需要使用微信的多列选择器。如果只是一列字段,或者每次拖动一次都去服务端取,会比较容易。 如果想一次定义好json,关联数据相…

eosjs-ecc中文文档
链客,专为开发者而生,有问必答! 此文章来自区块链技术社区,未经允许拒绝转载。 eosjs-ecc是eos官方处理密钥和签名的javascript开发包。访问地址:eosjs-ecc中文手册。 eosjs-ecc安装 nodejs环境下,使用N…
rocketmq 组监听_最全的RocketMQ学习指南,程序员必备的中间件技能
一、简介RocketMq是阿里开发出来的一个消息中间件,后捐献给Apache。官网上是这样介绍的: Apache RocketMQ™ is a unified messaging engine, lightweight data processing platform.RocketMQ是一个统一的处理消息引擎,轻量级的数据处理平台。…

【刷题】BZOJ 4516 [Sdoi2016]生成魔咒
Description 魔咒串由许多魔咒字符组成,魔咒字符可以用数字表示。例如可以将魔咒字符 1、2 拼凑起来形成一个魔咒串 [1,2]。 一个魔咒串 S 的非空字串被称为魔咒串 S 的生成魔咒。 例如 S[1,2,1] 时,它的生成魔咒有 [1]、[2]、[1,2]、[2,1]、[1,2,1] 五种…

jQuery的文档操作方法
jQuery 文档操作方法 这些方法对于 XML 文档和 HTML 文档均是适用的,除了:html()。 方法描述addClass()向匹配的元素添加指定的类名。after()在匹配的元素之后插入内容。append()向匹配元素集合中的每个元素结尾插入由参数指定的内容。appendTo()向目标结…

原 EOS智能合约开发入门
链客,专为开发者而生,有问必答! 此文章来自区块链技术社区,未经允许拒绝转载。 EOS智能合约的开发需要使用llvm和abigen来生成abi文件。 为此eos提供了一个 名为eosiocpp的工具。 在这篇文章中,我们介绍如何使用这个工…

python安装虚拟环境virtualenv
虚拟环境 虚拟环境是一个将不同项目所需求的依赖分别放在独立的地方的一个工具,它给这些工程创建虚拟的Python环境。它解决了“项目X依赖于版本1.x,而项目Y需要项目4.x”的两难问题,而且使你的全局site-packages目录保持干净和可管理。 比如&…

可变分区存储管理实验报告总结_操作系统实验报告-可变分区存储管理方式的内存分配回收...
一.实验目的(1)深入了解可变分区存储管理方式的内存分配回收的实现。二.实验内容编写程序完成可变分区存储管理方式的内存分配回收,要求有内存空间分配表,并采用最优适应算法完成内存的分配与回收。三.实验原理在可变分…

ubuntu/linuxmint如何添加和删除PPA源
【添加】 1、sudo add-apt-repository ppa:user/ppa-name 2、sudo apt-get update (然后再安装软件sudo apt-get install <package-name>或更新软件sudo apt-get upgrade) 【删除】 1、cd /etc/apt/source.list.d/ 2、sudo rm <ppa-name> 转载于:https://www.cnblo…

了解EOS看这一篇就够了一、团队二、技术三、项目进度四、争议和风险五、展望
链客,专为开发者而生,有问必答! 此文章来自区块链技术社区,未经允许拒绝转载。 无论是混迹于币圈、链圈还是矿圈,对BTC(比特币)、ETH(以太坊)、EOS这三大主流币一定不会…
qt 多个模型如何显示在表格中_Qt MOOC系列教程 第五章第四节:QML中的C++模型
我们已经多次讨论过如何创建自己的模型来表示QML中的数据,并且在上一节中我们看到了QStandardItemModel的基本示例。通常,出于性能和功能方面的原因,需要从一开始就要实现自己的模型。QAbstactItemModel类为项目模型类提供了抽象接口…

ubuntu终端基础命令
1. 启动终端的快捷键: ctr alt t2. 终端字体放大: ctrshift3. 终端字体放大: ctr-4. ls : 查看当前目录的文件信息 4.1 ls 路径: 查看指定目录的信息 4.1. pwd: 查看目录所在的路径5. touch: 创建文件 5.1 touch 1.txt 2.txt 创建多个文件6. mkdir: 创建…
